Ubuntu (IPA: [uːˈbuːntuː] in English, [ùɓúntú] in Zulu) is a computer operating system. It has consistently been rated among the most popular of the many Linux distributions. Ubuntu's goals include providing an up-to-date yet stable Linux distribution for the average user and having a strong focus on usability and ease of installation. Ubuntu is a derivative of Debian, another free operating system. Ubuntu is sponsored by Canonical Ltd, which is owned by South African entrepreneur Mark Shuttleworth. The word ubuntu is Zulu for "humanity". This Linux distribution is named as such to bring the spirit of the philosophy to the software world. Ubuntu is free software and can be shared by any number of users.
Kubuntu and Xubuntu are official subprojects of the Ubuntu project, aiming to bring the KDE and Xfce desktop environments, respectively, to the Ubuntu core (by default Ubuntu uses GNOME for its desktop environment). Edubuntu is an official subproject designed for school environments and should be equally suitable for children to use at home. Gobuntu is an official subproject that is aimed at adhering strictly to the Free Software Foundation's Four Freedoms. Ubuntu JeOS (pronounced "Juice") is the newest official subproject. JeOS is a concept for what an operating system should look like in the context of a virtual appliance.
Ubuntu releases new versions every six months, and supports those releases for 18 months with daily security fixes and patches to critical bugs. LTS (Long Term Support) releases, which occur every two years, are supported for three years for desktops and five years for servers. The most recent version, Ubuntu 8.04 LTS (Hardy Heron), was released on April 24, 2008, although an update, Ubuntu 8.04.1 LTS, was released on July 3, 2008. The next version will be 8.10 (Intrepid Ibex) and is scheduled for release in October 2008.
History and development process
Ubuntu's first release was on October 20, 2004, as a temporary fork of the Debian project. This was done so that a new version of Ubuntu could be released every six months, resulting in a more frequently updated system. Ubuntu releases always include the most recent GNOME release, and are scheduled to be released about a month after GNOME. In contrast with previous general-purpose forks of Debian—such as MEPIS, Xandros, Linspire, Progeny and Libranet, many of which relied on proprietary and closed source add-ons as part of their business model—Ubuntu has stayed closer to Debian's philosophy and uses free (libre) software most of the time.
The Ubuntu logo and typography has remained the same since that first release. The hand-drawn, lowercase OpenType font used is called Ubuntu-Title and was created by Andy Fitzsimon.The font is distributed under the terms of the GNU Lesser General Public License (LGPL) and use with logos derived from the Ubuntu logo is encouraged.The font is available as a package for Ubuntu.
Ubuntu packages have generally been based on packages from Debian's unstable branch: both distributions use Debian's deb package format and APT/Synaptic to manage installed packages, although Debian and Ubuntu packages are not necessarily binary compatible with each other. Ubuntu cooperates with Debian—to some extent pushing changes back to Debian, although there has been criticism concerning lack of occurrence. Many Ubuntu developers are also maintainers of key packages within Debian. However, Ian Murdock, the founder of Debian, criticized Ubuntu packages for incompatibilities with Debian, saying Ubuntu had diverged too far from Debian Sarge to remain compatible.
Ubuntu is currently funded by Canonical Ltd. On July 8, 2005, Mark Shuttleworth and Canonical Ltd announced the creation of the Ubuntu Foundation and provided an initial funding of US$10 million. The purpose of the foundation is to ensure the support and development for all future versions of Ubuntu. Mark Shuttleworth describes the foundation as an emergency fund in case Canonical's involvement ends.
Ubuntu 8.04, released on April 24, 2008, is the current Long Term Support (LTS) release. Canonical has released previous LTS versions separated by two years, and has committed to releasing the next LTS version in 2010, two years after 8.04.
Vendor support
A number of vendors offer computers with Ubuntu pre-installed. Dell and Tesco[25] have provided this option since 2007, while System 76 has done so since November 2005.[26] Dell and System76 customers are able to choose between 30-day, three-month, and yearly Ubuntu support plans through Canonical, Ubuntu's parent company. Dell has increased the availability of Ubuntu-driven computers by offering them for sale in the United Kingdom, France, Germany, Canada, Spain, and Latin America. Selected Dell machines running Ubuntu 7.10 and 8.04 have proprietary, legal DVD playback capabilities using LinDVD. Dell computers running Ubuntu 8.04 include extra support for ATI Video Graphics, Dell Wireless, Fingerprint Readers, HDMI, Bluetooth and MP3/WMA/WMV
Features

A screenshot of Ubuntu 6.06 LTS, showing the Dawn of Ubuntu wallpaper
Ubuntu focuses on usability, including the widespread use of the sudo tool for administrative tasks. The Ubiquity installer allows installing Ubuntu to the hard disk from within the Live CD environment without the need for restarting the computer prior to installation. Ubuntu also emphasizes accessibility and internationalization, to reach as many people as possible. Beginning with 5.04, UTF-8 became the default character encoding. The default appearance of the user interface in the current version is called Human and is characterized by shades of brown and orange.
The most recent version of Ubuntu comes installed with a wide range of software including: the OpenOffice.org productivity suite, the internet browser Firefox, the instant messenger Pidgin (formerly known as Gaim), the BitTorrent client Transmission and the raster graphics editor GIMP. Several lightweight card, puzzle games, and board games are pre-installed including Sudoku and chess. Ubuntu has all networking ports closed by default for added security, although its firewall, which offers more fine-grained control of incoming and outgoing connections, is installed but not enabled. Ubuntu is available in many languages. GNOME 2.22—the default desktop environment of Ubuntu 8.04—offers support for 46 languages. There are numerous ways to install Ubuntu.
Alternate Installation
In addition to the Live CD, Ubuntu can be installed through alternate methods. One such method is the alternate install CD.
The alternate install CD is an alternative installation disk designed for specialist installations of Ubuntu by providing a text-based rather than graphical installation. The alternate install CD allows for the creation of pre-configured OEM systems, for the upgrading of older installations without network access, and for installation on systems with less than 320 MB of RAM. The alternate install CD also allows LVM and/or RAID partitioning to be set up, as well as the encryption of partitions using dm-crypt. The alternate install CD is not a Live CD.

Default login screen for Ubuntu 8.04 (Hardy Heron)'s server edition
Ubuntu can also be installed over a network via the network install CD. The network install CD installs Ubuntu directly from an Ubuntu mirror. Installation from a mirror ensures that installed packages are up-to-date. The network install CD contains only the kernel, to start up the installation. The installation is text-based.
The final alternate installation method is used to install Ubuntu Server. The server install CD contains all packages needed for installation without a network connection. The server installation of Ubuntu does not install a graphical user interface.
Package classification and support

Ubuntu 8.04 CD
Ubuntu divides all software into four domains to reflect differences in licensing and the degree of support available. They are as follows:
Free software here includes only that which meets the Ubuntu licensing requirements, which roughly correspond to the Debian Free Software Guidelines. There is one exception for the Main category, however — it contains firmware and fonts which are not allowed to be modified, but are included because their distribution is otherwise unencumbered.
Non-free software is usually unsupported (Multiverse), but some exceptions (Restricted) are made for very important non-free software. Supported non-free software includes device drivers that are necessary to run Ubuntu on current hardware, such as binary-only graphics card drivers. The level of support in the Restricted category is more limited than that of Main, since the developers may not have access to the source code. It is intended that Main and Restricted should contain all software needed for a general-use Linux system. Alternative programs for the same tasks and programs for specialized applications are placed in the Universe and Multiverse categories.
Besides the official repositories is Ubuntu Backports, which is an officially recognized project to backport newer software from later versions of Ubuntu. The repository is not comprehensive; it consists primarily of user-requested packages, which are approved if they meet quality guidelines.
Availability of proprietary software
- See also: Linux distribution#Proprietary software and Medibuntu
Ubuntu has a certification system for third party software. Proprietary software certified with Ubuntu should work well in Ubuntu. However, many programs familiar to users of non-free operating systems, such as Microsoft Windows, are incompatible and are not Ubuntu-certified. Some proprietary software that does not limit distribution is included in Ubuntu's multiverse component. The package ubuntu-restricted-extras additionally contains software that may be legally restricted, including support for MP3 and DVD playback, Microsoft TrueType core fonts, Sun's Java runtime environment, Adobe's Flash Player plugin, many common audio/video codecs, and unrar, an unarchiver for .rar files.
Releases
Each release has both a code name and a version number. The version number is based on the year and month of release. For example, the very first release of Ubuntu 4.10 was released on October 20, 2004. Consequently, version numbers for future versions are provisional; if the release is delayed until a different month to that planned, the version number changes accordingly. The first characters of release names form an alphabetical series. This makes it easier to determine which release is newer when comparing two. Exceptions are the first few releases that should have begun with A, B, C.
Releases are timed to be approximately one month after GNOME releases, which are in turn about one month after releases of X.org. Consequently, every Ubuntu release comes with a newer version of both GNOME and X. Release 6.06—and recently 8.04—have been labeled as a Long Term Support (LTS), to indicate support with updates for three years on the desktop and five years on the server, with paid technical support available from Canonical Ltd.
Ubuntu 4.10 (Warty Warthog)

Ubuntu 4.10
(Warty Warthog)
Ubuntu 4.10 (Warty Warthog), released on 2004-10-20,[45] was Canonical's first release of Ubuntu Linux, building upon Debian GNU/Linux with plans for a new release every six months and eighteen months of support thereafter. Ubuntu 4.10's support ended on 2006-04-30. Ubuntu 4.10 was the first version of Ubuntu to offer ShipIt services, allowing users to order free install CDs. The desktop version included, among other desktop programs, Gaim 1.0, GIMP 2.0, GNOME 2.8, Mozilla Firefox 0.9, and OpenOffice.org 1.1. The server version shipped with MySQL 4.0, PHP 4.3, and Python 2.3. Ubuntu 4.10 used Linux 2.6.8 kernel with XFree86 4.3.
Ubuntu 5.04 (Hoary Hedgehog)

Ubuntu 5.04
(Hoary Hedgehog)
Ubuntu 5.04 (Hoary Hedgehog), released on 2005-04-08,[33] was Canonical's second release of Ubuntu Linux. Ubuntu 5.04's support ended on 2006-10-31. Ubuntu 5.04 added many new features including an update manager, upgrade notifier, readahead and grepmap, suspend, hibernate and standby support, dynamic frequency scaling for processors, ubuntu hardware database, Kickstart installation, and APT authentication. Ubuntu 5.04 allowed installation from USB devices. Ubuntu 5.04 used UTF-8 by default.
The desktop installation of Ubuntu 5.04 included, among other programs, Gaim 1.1, GIMP 2.2, GNOME 2.10, Mozilla Firefox 1.0, and OpenOffice.org 1.1. The server installation included MySQL 4.0, PHP 4.3, and Python 2.4. Ubuntu 5.04 used Linux 2.6.10 and X.Org 6.8.
Ubuntu 5.10 (Breezy Badger)

Ubuntu 5.10
(Breezy Badger)
Ubuntu 5.10 (Breezy Badger), released on 2005-10-13,[53][54] was Canonical's third release of Ubuntu Linux. Ubuntu 5.10's support ended on 2007-04-13.[55] Ubuntu 5.10 added several new features including a graphical bootloader (Usplash), an Add/Remove Applications tool, a menu editor (alacarte), an easy language selector, logical volume management support, full Hewlett-Packard printer support, OEM installer support, and Launchpad integration for bug reporting and software development.
The desktop installation of Ubuntu 5.10 included, among other programs, Gaim 1.5, GIMP 2.2, GNOME 2.12, Mozilla Firefox 1.0, and OpenOffice.org 1.9 (pre-2.0 release). The server installation included MySQL 4.1, PHP 5.0, and Python 2.4. Ubuntu 5.10 used Linux 2.6.12 and X.Org 6.8.
Ubuntu 6.06 (Dapper Drake)

Ubuntu 6.06
(Dapper Drake)
Ubuntu 6.06 (Dapper Drake), released on 2006-06-01,[58][59] was Canonical's fourth release, and the first Long Term Support (LTS) release. Ubuntu 6.06's support will end in June 2009 for desktops and June 2011 for servers. Ubuntu 6.06 included several new features, including having the Live CD and Install CD merged onto one disc, a graphical installer on Live CD (Ubiquity), Usplash on shutdown as well as startup, a network manager for easy switching of multiple wired and wireless connections, Humanlooks theme implemented using Tango guidelines, based on Clearlooks and featuring orange colors instead of brown, and GDebi graphical installer for package files. Ubuntu 6.06 did not include a means to install from a USB device, but did for the first time allow installation directly onto removable USB devices.
The desktop installation of Ubuntu 6.06 included, among other programs, Gaim 1.5, GIMP 2.2, GNOME 2.14, Mozilla Firefox 1.5, and OpenOffice.org 2.0. The server installation included MySQL 5.0, PHP 5.1, and Python 2.4, as well as an option to install LAMP. Ubuntu 6.06 used Linux 2.6.15 and X.Org 7.0.
Ubuntu 6.10 (Edgy Eft)

Ubuntu 6.10
(Edgy Eft)
Ubuntu 6.10 (Edgy Eft), released on 2006-10-26, was Canonical's fifth release of Ubuntu Linux. Ubuntu 6.10's support ended on 2008-04-25. Ubuntu 6.10 added several new features including a heavily modified Human theme, Upstart init daemon, automated crash reports (Apport), Tomboy note taking application, and F-spot photo manager. EasyUbuntu, a third party program designed to make Ubuntu easier to use, was included in Ubuntu 6.10 as a meta-package.
The desktop installation of Ubuntu 6.10 included, among other programs, Gaim 2.0, GIMP 2.2, GNOME 2.16, Mozilla Firefox 2.0, and OpenOffice.org 2.0. The server installation included MySQL 5.0, PHP 5.1, and Python 2.4. Ubuntu 6.10 used Linux 2.6.17 and X.Org 7.1.
Ubuntu 7.04 (Feisty Fawn)

Ubuntu 7.04
(Feisty Fawn)
Ubuntu 7.04 (Feisty Fawn), released on 2007-04-19, was Canonical's sixth release of Ubuntu Linux. Ubuntu 7.04's support will end in October 2008. Ubuntu 7.04 included several new features, among them a migration assistant to help former Microsoft Windows users transition to Ubuntu, support for Kernel-based Virtual Machine, assisted codec and restricted drivers installation, Compiz desktop effects, support for Wi-Fi Protected Access, the addition of Sudoku and chess, a disk usage analyzer (baobab), GNOME Control Center, and Zeroconf support for many devices. Ubuntu 7.04 dropped support for PowerPC architecture.
The desktop installation of Ubuntu 7.04 included, among other programs, Gaim 2.0, GIMP 2.2, GNOME 2.18, Mozilla Firefox 2.0, and OpenOffice.org 2.2. The server installation included MySQL 5.0, PHP 5.2, and Python 2.5. Ubuntu 7.04 used Linux 2.6.20 and X.Org 7.2.
Ubuntu 7.10 (Gutsy Gibbon)
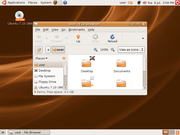
Ubuntu 7.10
(Gutsy Gibbon)
Ubuntu 7.10 (Gutsy Gibbon), released on 2007-10-18, was Canonical's seventh release of Ubuntu Linux. Ubuntu 7.10's support will end in April 2009. Ubuntu 7.10 included several new features, among them AppArmor security framework, fast desktop search, a firefox plug-in manager (Ubufox), a graphical configuration tool for X.org[73] full NTFS support (read/write) via NTFS-3G, and a revamped printing system with PDF printing by default. Compiz Fusion was enabled as default in Ubuntu 7.10 and Fast user switching was added.
The desktop installation of Ubuntu 7.10 included, among other programs, GIMP 2.4, GNOME 2.20, Mozilla Firefox 2.0, OpenOffice.org 2.3, and Pidgin 2.2. The server installation included MySQL 5.0, PHP 5.2, and Python 2.5. Ubuntu 7.10 used Linux 2.6.22 and X.Org 7.2.
Ubuntu 8.04 (Hardy Heron)

Ubuntu 8.04
(Hardy Heron)
Ubuntu 8.04 (Hardy Heron), released on 2008-04-24, is Canonical's eighth and latest release of Ubuntu Linux. It is the second Long Term Support (LTS) release. Ubuntu 8.04's support will end in April 2011 for desktops and April 2013 for servers. Ubuntu 8.04 included several new features, among them Tracker desktop search integration, Brasero disk burner, Transmission BitTorrent client, Vinagre VNC client, system sound through PulseAudio[80], and Active Directory authentication and login using Likewise Open. In addition Ubuntu 8.04 included updates for better Tango compliance, various Compiz usability improvements, automatic grabbing and releasing of the mouse cursor when running on a VMware virtual machine, and an easier method to remove Ubuntu. Ubuntu 8.04 is the first version of Ubuntu to include the Wubi installer on the LiveCD that allows Ubuntu to be installed as a single file on a Windows hard drive without the need to repartition the disk.
The desktop installation of Ubuntu 8.04 included, among other programs, GIMP 2.4, GNOME 2.22, Mozilla Firefox 3.0 Beta 5, OpenOffice.org 2.4, and Pidgin 2.4. The server installation included MySQL 5.0, PHP 5.2, Python 2.5. Ubuntu 8.04 uses Linux 2.6.24 and X.Org 7.3.
Ubuntu 8.10 (Intrepid Ibex)

Ubuntu 8.10 Alpha 1
(
Intrepid Ibex)
Ubuntu 8.10 (
Intrepid Ibex), to be released on
2008-
10-30,will be Canonical's ninth release of Ubuntu. It will be supported until April 2010. Ubuntu 8.10 has several planned new features including a complete desktop redesign, improvements to mobile computing and desktop scalability, increased flexibility for Internet connectivity,
OpenGL face browser for
GDM, a
GUI driven
Live USB creator and an encrypted 'private' directory in each user's home directory.
|
| Company / developer | Canonical Ltd. / Ubuntu Foundation |
| OS family | Linux, Unix-like |
| Working state | Stable |
| Source model | Free and open source software |
| Initial release | October 20, 2004 (2004-10-20) |
| Latest stable release | 8.04.1 (Hardy Heron)/ July 3, 2008 (2008-07-03); 24 days ago |
| Latest unstable release | 8.10 Alpha 3 (Intrepid Ibex)/ 7-24-2008 |
| Available language(s) | Multilingual (more than 55) |
| Update method | APT |
| Package manager | dpkg (Debian GNU/Linux Package Manager) |
| Supported platforms | i386, AMD64, IA-64, UltraSPARC[a], PowerPC ( PowerPC support to be dropped)[b] |
| Kernel type | Monolithic (Linux) |
| Default user interface | GNOME, KDE (see Kubuntu), XFCE (see Xubuntu) |
| License | Various, primarily GPL and GFDL |
| Website | www.ubuntu.com |


























